IXmaps: Frequently Asked Questions
What is IXmaps?
The IXmaps research project has developed an interactive mapping tool that enables Internet users to view the routes that data packets take across the Internet, with surveillance and other interesting features highlighted along the way. The initiative also includes annual reports on the privacy transparency ratings of Internet carriers that route Canadian traffic.
The IXmaps project is led by Professor Andrew Clement and comprises a team of privacy and Internet experts at the University of Toronto and York University. To learn more, check out their What is IXmaps? video.
What does the “IX” in “IXmaps” stand for?
The IX stands for Internet Exchange. We like to think of the Internet as a cloud, but most of it relies on a select few buildings — called Internet Exchanges — that connect the most important Internet cables together. Internet Service Providers and Content Delivery Networks use these key buildings to exchange traffic between their networks.
Although Internet Exchanges are a very important part of the global Internet infrastructure, their physical nature can make them, and us, vulnerable to surveillance. For example, the U.S. National Security Agency (NSA) has installed listening posts — or ‘splitter rooms’ — in major Internet Exchanges across the United States, enabling it to collect all data passing through them.
As a Canadian, why does it matter where my data travels?
There have been countless revelations of U.S. mass surveillance over the past few years, and it can be easy for Canadians to think that those problems don’t impact us — but they do. A substantial amount of our daily activities online are actually routed through the U.S., even when we’re accessing Canadian content from within Canada.
One of the biggest problems with this situation is that the NSA has installed listening posts in a large number of U.S. cities where Internet Exchanges are located. If your data travels through the U.S., it passes through one of these cities, and is subject to being monitored by the NSA, with information about you collected, analyzed, and stored at the main NSA Data Center in Utah. Once outside Canada, your data is treated by the NSA as foreign and loses Canadian legal and constitutional protections. This represents a major loss of privacy.
Tell me more about the privacy implications of NSA monitoring?
The fact that so much Canadian data is subject to NSA surveillance raises profound privacy concerns. Leaked documents have confirmed that the NSA conducts sweeping surveillance of all international communications. This surveillance is conducted indiscriminately, meaning there’s no need to ‘have something to hide’ to be affected by it — it impacts everyone.
When your private communications metadata is collected in bulk in this way, experts warn that it enables the NSA to paint a detailed picture of your personal life, including your financial status, medical conditions, sexual orientation, and even your political or religious beliefs.
By collecting this kind of information in bulk, the government of the day — no matter who it is — can at the push of a button bring up an intimate portrait of almost any law-abiding citizen, regardless of whether they’ve been involved in any wrongdoing. (For more on how your metadata can be used in this way, check out A Primer on Metadata: Separating Fact and Fiction by Ontario’s former privacy commissioner Ann Cavoukian).
Does NSA monitoring apply when I visit websites or communicate with someone inside Canada?
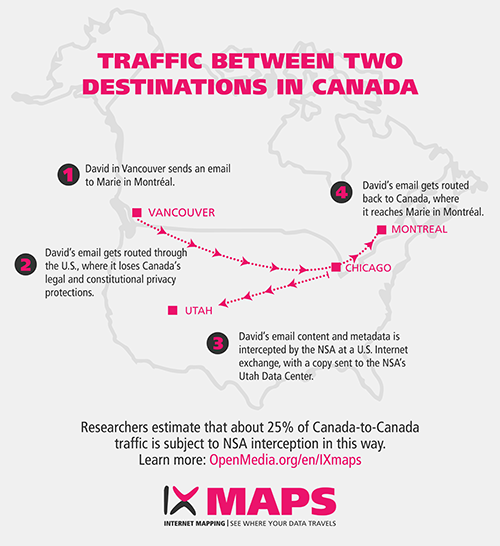
Yes. Even ‘domestic’ Canada-to-Canada data can be subject to NSA surveillance when it travels through the U.S. For example, an email sent from a server in Vancouver to one in Montréal may travel through multiple U.S. cities on its way to its destination. Even an email sent from Vancouver to a destination also in Vancouver can travel via the U.S. using what are known as ‘boomerang’ routes.
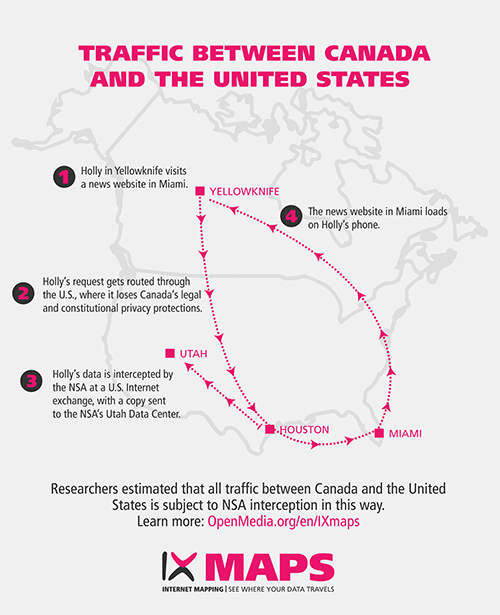
What’s even more concerning is that this type of monitoring does not apply solely to emails. For example, a Canadian visiting a domestic Canadian website (such as the Globe & Mail or CBC News) is also vulnerable to having their traffic travel through the U.S. where it gets monitored by the NSA. Perhaps you may not care if the NSA knows which CBC stories you read that morning — but what if you were visiting a Canadian HIV/Aids support website, or a suicide prevention hotline?
What is a ‘boomerang’ route?
A boomerang route is a data packet path that starts and ends in Canada, but travels through the U.S. for part of the journey. Researchers at IXmaps have found that a lot of Canadian Internet traffic is routed in this way, even though may originate and have an end destination in the same city.
Here’s an example of a typical boomerang route, showing the path that data took when someone from their home in Toronto accessed the Toronto Star’s website:
Despite being hosted only a few kilometers away from the user, the data traveled through New York City and Chicago, both cities where the NSA has installed surveillance facilities in the large Internet traffic exchanges, before returning to Toronto.
Can you show me more examples of how Canadian Internet traffic is vulnerable to NSA interception?
Whether a Canadian is communicating with a website or individual within Canada, within the U.S., or within a third country, their data may be vulnerable to NSA interception.
Here are some illustrative depictions of how that interception takes place:
Scenario 1: Traffic between two destinations in Canada:
Scenario 2: Traffic between Canada and the U.S.
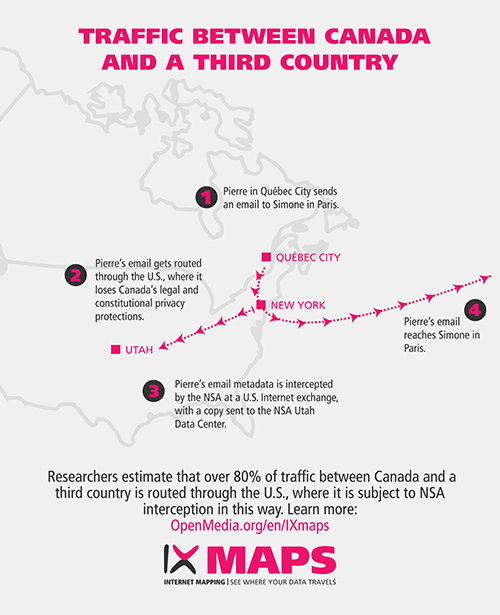
Scenario 3: Traffic between Canada and a third country
Where can I learn more about how my traffic travels across the Internet?
IXmaps researchers have developed an innovative Internet mapping database at IXmaps.ca, that allows you to see how Canadians’ personal data travels across the Internet. To date, users have contributed data that has helped map over 150,000 traceroutes in this tool’s database. You can explore them for yourself right here.
The IXmaps site enables you to selectively map routes based on your preferred locations, ISPs, destinations, etc., and to see whether these routes pass through sites of suspected NSA surveillance. Early in the new year, the IXmaps researchers will be launching an upgraded version — and we’ll be sure to let you know when it is ready for use!
What percentage of Canadian traffic winds up being subject to NSA surveillance?
It is challenging to estimate how much Canadian Internet traffic is routed through U.S. Internet Exchanges, where it is subject to NSA surveillance. If we define Canadian traffic as “all Internet traffic originating in Canada” — regardless of whether destined for sites in Canada, the U.S., or third countries, then this figure will be very high. For example, Professor Ron Deibert, director of the University of Toronto’s Citizen Lab, has estimated that at least 90% of Canadian Internet traffic is routed through U.S. exchange points. In part, this is because so much Canadian traffic is destined for popular U.S.-based services such as Google, Facebook, Twitter, etc.
When it comes to domestic traffic — origin and destination both in Canada — then IXmaps data suggests about 25% is routed via the U.S.
When it comes to traffic that originates in Canada and is destined for third countries (i.e. outside Canada and the U.S.), Professor Andrew Clement, the IXmaps project lead, notes that “much of Canadian international internet communications with countries other than the U.S. show similar ‘boomerang’ characteristics, in the sense that the traffic passes through the U.S., almost invariably via a city where the NSA has splitter interception facilities.”
The IXmaps database currently contains 7,233 routes that either originate in Canada and terminate somewhere outside Canada and the U.S., or originate outside of Canada and the U.S. and terminate inside Canada. A whopping 81% of these routes transited the U.S.
Why is so much of our traffic to third countries routed through the U.S., where it’s vulnerable to being monitored by the NSA?
A big reason is that the vast majority of Internet traffic between North America and Europe, and between North America and Asia, travels the Atlantic and Pacific oceans through fibre-optic cables — and most of these cables land in the U.S. rather than Canada.
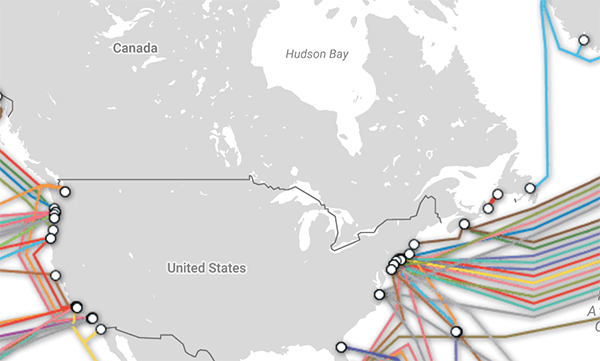
Of 13 trans-Pacific fibre-optic cables, all 13 land on the U.S. west coast, with none landing in Canada.
Of 14 trans-Atlantic fibre-optic cables, 12 land on the U.S. east coast, while only 2 landing in Canada.
To learn more about where these cables are located, check out TeleGeography’s interactive Submarine Cable Map.
Just two trans-Atlantic fibre-optic cables land in Canada, compared with 12 in the U.S. (Creative Commons image from TeleGeography Telecom Resources)
What can be done to keep more Canadian traffic in Canada?
By keeping more domestic Canadian traffic within Canada, we can reduce our collective exposure to NSA surveillance activities.
IXmaps researchers Andrew Clement and Jonathan Obar have made a number of specific recommendations to help create a Canadian network architecture and Internet policy that is more likely to ensure that domestic Canadian traffic does not ‘boomerang’ to the U.S. and back. They include:
Building up our domestic infrastructure by creating new Canadian Internet exchanges — this will make it much more likely that Canada-to-Canada traffic stays within our borders, all while promoting more efficient routing. The Canadian Internet Registration Authority (CIRA) is already fostering the development of more Internet exchanges within Canada, for both economic and privacy reasons.
Expanding Canada’s long-haul Internet backbone capacity — imagine your Internet traffic is a car traveling on a highway. Here in Canada, most of what we’ve built when it comes to the Internet are the equivalent of narrow two-lane roads. But say you’re traveling from Vancouver to Halifax — you’d want to be on a highway instead of a back road. Investing in this long-haul capacity to upgrade Canada’s Internet infrastructure to the equivalent of a four-lane highway will make it more likely that data traveling long distances from one location in Canada to another will stay within our borders, rather than boomerang through the U.S.
Ensuring that government procurement policies give greater priority to all-Canadian routing and privacy protection.
Requiring greater transparency and accountability on the part of Canadian telecom carriers in terms of their internetwork routing practices, long-haul carriage capacity and utilization, and data-protection provisions in the contractual arrangements with transit providers.
On the whole, the authors conclude that we need a “greater assertion of Canadian network sovereignty within the norms of a free and democratic society.”
You can dig more into Andrew Clement and Jonathan Obar’s detailed recommendations by checking out their chapter (pages 13-44) in Michael Geist (ed), Law, Privacy and Surveillance in Canada in the Post- Snowden Era, which is available for free, open access download at http://www.press.uottawa.ca/law-privacy-and-surveillance or http://hdl.handle.net/10393/32424
What is the NSA’s PRISM program, and how does it impact my privacy?
The NSA’s PRISM program systematically collects private Internet communications from popular services including Facebook, Gmail, Hotmail, Skype, YouTube, and many other services. Depending on the source, the program enables the NSA to collect vast quantities of emails, chat (video and voice), videos, photos, stored data, and social networking details.
First revealed by whistleblower Edward Snowden, PRISM represents a very significant threat to the privacy of Canadians (and anyone else) who uses these popular online services.
It’s important to note that there is an important distinction between how the NSA collects your private data via the PRISM program, and how it collects your data by intercepting it in transit:
With PRISM, the NSA collects the data directly from the Internet companies involved.
In transit, the NSA collects your data with its Upstream programs, scooping up data from the Internet exchanges it passes through — effectively capturing it while it is going from one destination to another.
While the IXmaps project deals with the latter phenomenon rather than PRISM, we thought that PRISM was important to include in this FAQ given the significant privacy risks it poses to Canadians.
What are some other significant threats to the online privacy of Canadians?
Sadly, Canadians face a deeply troubling privacy deficit. The previous federal government passed legislation such as Bill C-51 and Bill C-13, that dramatically expanded the power of the state to spy on the private lives of citizens, in many cases without a warrant.
As whistleblowers like Edward Snowden have revealed, Canada’s spy agencies — the CSE and CSIS — have long been engaged in activities that systematically attack and undermine the privacy of Canadians, and of innocent people all over the world. These agencies often work extremely closely with the U.S. NSA to achieve these goals.
To cap it all off, we’ve also seen a whole series privacy breaches from both federal and provincial governments. Former Privacy Commissioner Jennifer Stoddart, for example, calculated that about 725,000 Canadians had been affected by privacy breaches over a 10 year period, and that was just at the federal level.
All of this is deeply concerning, because a key foundation stone of any healthy democracy is that its citizens have a right to a private life. Everyone has things we prefer to keep private — perhaps a late night email to a friend, for example, or a harmless-yet-embarrassing health issue, or a set of disappointing exam results.
Preferring to keep some things to ourselves or those we trust is a hallmark of what it is to be human. In fact, privacy is, quite simply, the right to be ourselves. When that right is violated, it can results in self-censorship, a chill on political speech, a lack of willingness to challenge societal norms and the stifling of new thinking on any number of issues.
How does Bill C-51 impact my privacy?
Bill C-51 was passed by the former Conservative federal government in 2015. When this legislation was proposed, it saw huge public outcry — over 300,000 Canadians have called for its repeal. Despite promises from the current Liberal government to amend the bill, no such amendments have been made at the time of writing, although an extensive consultation on national security and Bill C-51 has been taking place.
Bill C-51 contains a number of deeply troubling proposals. It expands the powers of CSIS to the point where the Globe and Mail’s editorial team warned it amounts to the creation of a “secret police force”. Some of the most concerning aspects of Bill C-51 include:
Enabling detention without charge for up to 7 days;
Allowing CSIS to interfere with and “disrupt” people or organizations it views as a “threat to the security of Canada”;
Defining these “security threats” in an overly-broad way — environmentalists, peaceful protestors, even democratic Quebec secessionists could be targeted.
Containing such a vague definition of “terrorist propaganda” that it effectively criminalizes free expression online;
Making it far easier for CSIS to place Canadians on a no-fly list with no effective right to appeal;
Facilitating information sharing on innocent Canadians, amounting to a surveillance dragnet;
Permitting CSIS to undertake illegal activity and breach Charter rights of individual Canadians. The legislation doesn’t specify what such illegal activities may include, although it does prohibit CSIS from torture, murder, or “violating the sexual integrity” of an individual.
You can learn more by checking out Bill C-51: A Primer, which is jointly published by OpenMedia, Canadian Journalists for Free Expression, and the Canadian Internet Policy and Public Interest Clinic. Professors Craig Forcese and Kent Roach have also written extensively on Bill C-51, and much of their work is freely available at AntiTerrorLaw.ca
Tell me more about the Communications Security Establishment (CSE), its relationship to the NSA, and the impact of its activities on my privacy?
The Communications Security Establishment (CSE) is Canada’s electronic eavesdropping agency. CSE works extremely closely with its counterparts in the U.S. NSA, the UK’s GCHQ, Australia’s ASIO, and New Zealand’s GCSB.
Together these agencies are referred to as the ‘Five Eyes’ and their relationship is so close that Edward Snowden has described them as “sort of a supranational intelligence organisation that doesn’t answer to the laws of its own countries.”
For years, these agencies have operated under a veil of near-total secrecy. But thanks to Edward Snowden and other whistleblowers, this veil of secrecy has recently been lifted to some extent.
We now know, for example, that the CSE, along with its ‘Five Eyes’ partners, is engaging in massive surveillance undertakings that are collecting, storing, and analyzing vast quantities of personal information and private communications from all over the world, including here in Canada.
Specific recent examples of CSE surveillance activities include:
Spying on thousands of innocent Canadian air-travellers passing through Pearson airport, and even monitoring their precise movements around the world for weeks (CBC)
The LEVITATION program monitors 15 million downloads EVERY DAY, with Canadians among the targets. (CBC)
Collecting emails that Canadians send to MPs, including viewing their content. (Global News)
Facilitating a massive U.S. spy operation on Canadian soil during the Toronto G-20 summit in 2010. (Toronto Star)
Spying on Brazil's Mining Ministry, and undermining a major relationship with an international ally. (The Guardian)
You can learn more about this topic by checking out Christopher Parsons’ Canadian SIGINT Summaries at: https://www.christopher-parsons.com/writings/cse-summaries/
What is metadata, and why is it so troubling that the NSA and CSE collects it in bulk?
Metadata is “data about data” — e.g. the header information of an email, or the bulk collection of phone records of “who called who, for how long, where and when.”
Metadata is usually presented by the pro-surveillance lobby as excluding the content of an email or a phone call — but when collected in bulk it can be even more invasive and revealing. Furthermore, it lacks the important legal protections that communications content does. This is why the bulk collection of metadata by the NSA (and other spy agencies including Canada’s CSE) is especially problematic.
Governments seeking to defend bulk metadata collection say it’s just looking at the “outside of an envelope” — but if that analogy were true, it would need to be a magic envelope, listing not just the sender and recipient, but also every previous time they had been in contact with each other, everyone else they had been in contact with, and even everyone who those people were in contact with. In short: metadata draws a detailed map of our lives.
To make matters worse, combining deep packet inspection and powerful search techniques, intelligence agency computers can analyse the content of intercepted messages looking for particular keywords or phrases. As long as no human reads the content they still treat the results as metadata with its significantly lower level of protection.
How revealing is metadata? Here’s what top experts have to say:
Citizen Lab’s Prof. Ron Deibert: Metadata is “way more powerful than the content of communications."
American Civil Liberties Union: Metadata "can paint a profoundly detailed picture of our lives."
Former Ontario Privacy Commissioner Ann Cavoukian: Metadata "can reveal a great deal about you as an individual."
Professor Andrew Clement: “Even basic metadata — number dialed, time of call, email address, geographic location, etc. — can in sufficient quantities be much more revealing of an individual’s behaviour, movements, beliefs and affiliations than previously understood.”
You can learn more about metadata and surveillance by reading Ann Cavoukian’s A Primer on Metadata: Separating Fact and Fiction.
Do Canadian telecom providers have a role to play in keeping my private data secure?
Telecommunications providers have a crucial role to play in terms of protecting the privacy of their customers. In Canada, the government has passed laws to force telecom providers to intercept communications, or to make it easier for government agencies to obtain our basic subscriber information.
Every day millions of Canadians entrust their Internet Service Provider (ISP) or mobile carrier with enormous quantities of sensitive, personal information. Against a backdrop of concerning revelations of mass surveillance, it’s more important than ever that ISPs be forthcoming about how they safeguard our personal information. ISPs can play a leadership role in working for strong data privacy protection.
How can I tell which telecom providers have my back when it comes to privacy?
As part of the IXmaps project, Professor Andrew Clement and Dr Jonathan Obar publish the Keeping Internet Users in the Know or in the Dark: Data Privacy Transparency of Canadian Internet Carriers reports, rating how transparent telecom providers are when it comes to safeguarding their customers’ privacy.
This report features an at-a-glance ‘Star Chart’, rating ISPs according to 10 key transparency criteria. You can find the most recent annual report here: https://www.ixmaps.ca/transparency.php
Are there tools I can use to help keep my data safe?
While no tool can ensure that your data stays within Canada, there are a range of easy-to-use practical tools that people can use to better protect their privacy online. The good news is that you don’t need to be a computer expert to take significant steps to safeguard yourself from mass surveillance.
These tools include:
Virtual Private Networks (VPNs): VPNs are probably the single easiest way to help safeguard your online privacy. When connected to a VPN, all of your Internet communications are encrypted and made secure from (most) eavesdropping. Instead of getting a list of websites you visit, a watcher can just tell you have connected to a VPN and nothing more. Practically everybody should be using a VPN, but many people still don’t. Although some VPNs are free, but you are better off investing the <$10 a month for a good one. (PC Magazine have published a list of top VPNs you can use as a starting point)
TOR (The Onion Router): TOR is free software that enables anonymous online communication. It prevents people from learning your location, or your browsing habits. It even prevents the sites you visit from learning your physical location. It works by routing your communications through many, many “layers” — like the layers of an onion, hence the name. You can download the free and easy-to-use Tor browser at www.TorProject.org
Encrypted mobile messaging apps: An increasing number of mobile messaging apps now feature end-to-end encryption — meaning the only person who can decrypt your message is the intended recipient. These apps are available for iPhones, Android, and most mobile operating systems. Great examples include Signal (recommended by Edward Snowden!), and Telegram.
PGP encryption: PGP (which stands for Pretty Good Privacy) is often used for encrypting and decrypting emails and texts. PGP users publish their Public Key — anyone can then use this to send that person an encrypted email that only they can read. It’s slightly less user-friendly than VPNs or TOR, but still pretty straightforward. You can learn more at https://en.wikipedia.org/wiki/Pretty_Good_Privacy
If you’re looking to learn more about protecting yourself from mass surveillance, but don’t know where to get started, the Electronic Frontier Foundation has excellent step-by-step guides to implementing many of the tools we’ve mentioned above on their Surveillance Self-Defensewebsite.
Where can I learn more about all this?
Coming clean on going dark - what can security services learn about you from metadata? (by Professor Andrew Clement)
IXmaps: see where your data goes (by our own Meghan Sali)
Canadian Internet traffic is travelling through the U.S., making Canadians even more vulnerable to NSA surveillance (by our own Laura Tribe)
The Protect our Privacy Coalition (dozens of organizations and experts are working together for stronger privacy rules)
Christopher Parsons’ Canadian SIGINT Summaries about CSE activities.
Access My Info - This tool from Citizen Lab and OpenEffect lets you find out what companies and the government have on file about you.
IXmaps: a tool to figure out when the NSA can see Canadians’ data (by Cory Doctorow, BoingBoing)
Canada’s Internet data “intimately linked” to U.S. networks: why you should be concerned (by Ryan Patrick, IT World Canada)
Canadian live route map highlights vulnerabilities to NSA spying efforts (by Kieren McCarthy, The Register)
Surveillance Self-Defense Toolkit (Electronic Frontier Foundation)
Acknowledgements:
OpenMedia is grateful for the support of the IXmaps team at University of Toronto and York University, who are working closely with us on this project.
This project was made possible by the financial support of the Office of the Privacy Commissioner of Canada.



 Take action now!
Take action now!
 Sign up to be in the loop
Sign up to be in the loop
 Donate to support our work
Donate to support our work